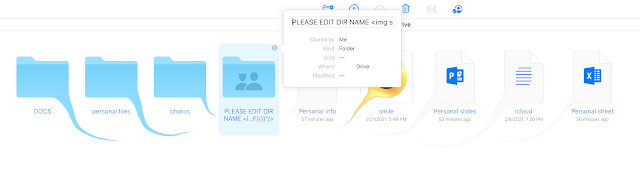
You may be wondering what this image means... This image is a summary of a potential attack vector I found on iCloud. While my image-handling skills may not be perfect, this post will provide you with a clear understanding by the end.
Introduction
In this post, I’ll share a vulnerability I discovered in iCloud, which could allow attackers to execute malicious code in other iCloud accounts. This article explores how the attack could be exploited and the potential damage attackers could inflict on victims’ accounts.
Apple paid me 9,000 USD through their bug bounty program.
Apple and the iCloud
In December 2020, I came across a tweet about a group of researchers who hacked Apple for 3 Months. In the blog post shared in the tweet, 55 vulnerabilities in the Apple domain are explained. After spending hours reading their detailed findings, I decided to attempt hacking Apple myself.
New writeup:
— Sam Curry (@samwcyo) October 8, 2020
"We Hacked Apple for 3 Months: Here’s What We Found"
Featuring...@bbuerhaus, @NahamSec, @erbbysam, and @_StaticFlow_ https://t.co/XE757tadE9
My strategy was to focus on a single target: iCloud. With limited time, narrowing my efforts to one specific target would maximize my chances of success.
The XSS Vulnerability
The vulnerability exploited is a Cross-site Scripting (XSS) vulnerability in the process of creating a file or folder in iCloud Drive.
Cross-site Scripting (XSS) is a type of security vulnerability that allows an attacker to execute malicious code on the victim’s browser. There are various methods to carry out such an attack. For a more detailed explanation, you can refer to this blog post by BugCrowd.
System Context
In iCloud Drive, users can upload files and organize them into folders.
In iCloud Drive, users can upload files and organize them into folders.
These folders and files can be shared with other iCloud users via email. Alternatively, users can make the file or folder public and share its link with anyone interested in accessing it.
In this context, the sharing functionality is crucial to the attack, as it allows the attacker to deliver the XSS payload to the victim through a shared file or folder.
The XSS...
Each folder or file has an icon that allows users to view its details or edit its name.
When the pop-up window is opened, an HTML <span> tag is injected into the DOM alongside other information.
Due to a server misconfiguration, an attacker could embed HTML tags into the directory name, which would then be loaded into the DOM.
With the ability to insert new elements into the DOM, the attacker could execute JavaScript code on the page.
The POC
In iCloud Drive, a strict Content Security Policy (CSP) was in place at that time, preventing me from using <script> tags or making requests to domains outside of *.icloud.com and *.apple.com. However, I was able to leverage event handlers to execute JavaScript via the XSS vulnerability.
Initially, I spent some time considering the potential impact of this XSS. After finding the vulnerability and a method to share it, I decided to immediately report it to Apple before someone else could exploit it.
A few days later, I sent the additional information to Apple to append further details to the original ticket.
In the final Proof of Concept (POC), the attacker shares a folder with the victim, where the folder name contains the following payload:
PLEASE EDIT DIR NAME <img src onerror="(function hacking(){//BAD JS STUFF}())"/>
PLEASE EDIT DIR NAME <img src onerror="(function hacking(){//BAD JS STUFF}())"/>
Inside the JavaScript function, I included code that made requests to iCloud APIs. These requests retrieved all file and folder IDs from the victim’s account and moved them into the folder shared by the attacker. This allowed the attacker to gain access to all of the victim’s files.
In the end, the XSS automatically moved all of the victim’s files into the attacker’s shared folder. This action corresponds to the image referenced at the beginning of this post.
Victim Interaction:
The XSS would only be fully exploited if the victim accepted the shared folder and opened the pop-up window. If the pop-up window remained unopened, the XSS would not execute.
Editable Name Issue:
When the attacker shares the malicious folder, the victim has the option to edit the folder name and remove the XSS payload. However, this change only occurs on the victim’s side. This means the attacker could repeatedly share the same malicious folder with multiple victims and gain access to files from all those who open the pop-up window.
Data Theft and Folder Removal:
Once the attacker gains access to the victim’s files inside the shared folder, they can stop sharing the folder to revoke the victim’s access. This effectively allows the attacker to steal all of the victim’s files.
Summary of the XSS Attack
This XSS vulnerability posed a significant risk to the CIA Triad, which is foundational to information security:
1. Confidentiality:
The attacker could access and exfiltrate all of the victim’s files and folders by moving them into a shared folder. This unauthorized access violated the confidentiality of the victim’s data.
2. Integrity:
By manipulating the victim’s file structure and moving files to the attacker’s shared folder, the integrity of the victim’s data was compromised. The attacker altered the data’s location and potentially its original organization, which could disrupt workflows or cause confusion for the victim.
3. Availability:
Once the attacker revoked the victim’s access to the shared folder, the victim could no longer access their own files. This directly impacted the availability of the victim’s data, rendering it inaccessible and resulting in a full-scale denial of access.
In this way, the attacker leveraged the XSS vulnerability to violate all three principles of the CIA Triad, making it a critical issue. By exploiting this flaw, the attacker could steal the victim’s data, manipulate its organisation, and ultimately deny access, achieving a complete data-theft attack.
Triage Dates
• 25/01/2021 – Opened
• 01/02/2021 – Re-tested (fixed)
• 02/02/2021 – Hall of Fame credit
• 16/02/2021 – Bounty awarded
I have to admit, the first and second weeks of February were quite stressful for me as I anxiously waited for updates from Apple. However, in the end, I was thrilled to receive that much-anticipated email confirming the recognition of my efforts.
Final Thoughts
This is my first write-up, and achieving this milestone means a lot to me. It represents a significant achievement in a short period of learning, and I’m proud of what I accomplished. One of my initial goals when I began this journey was to discover a vulnerability and write a detailed report about it.
Thanks for reading it!